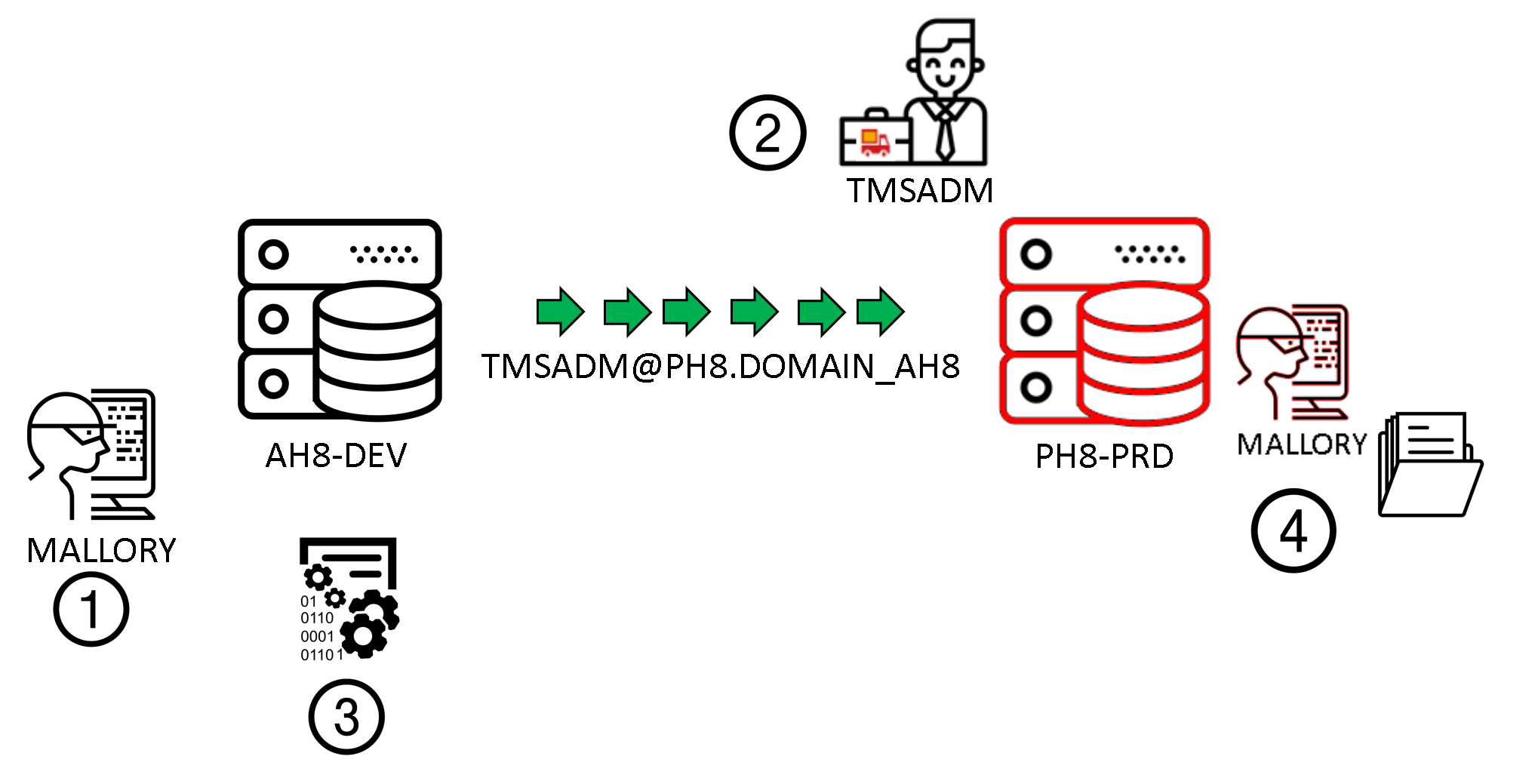
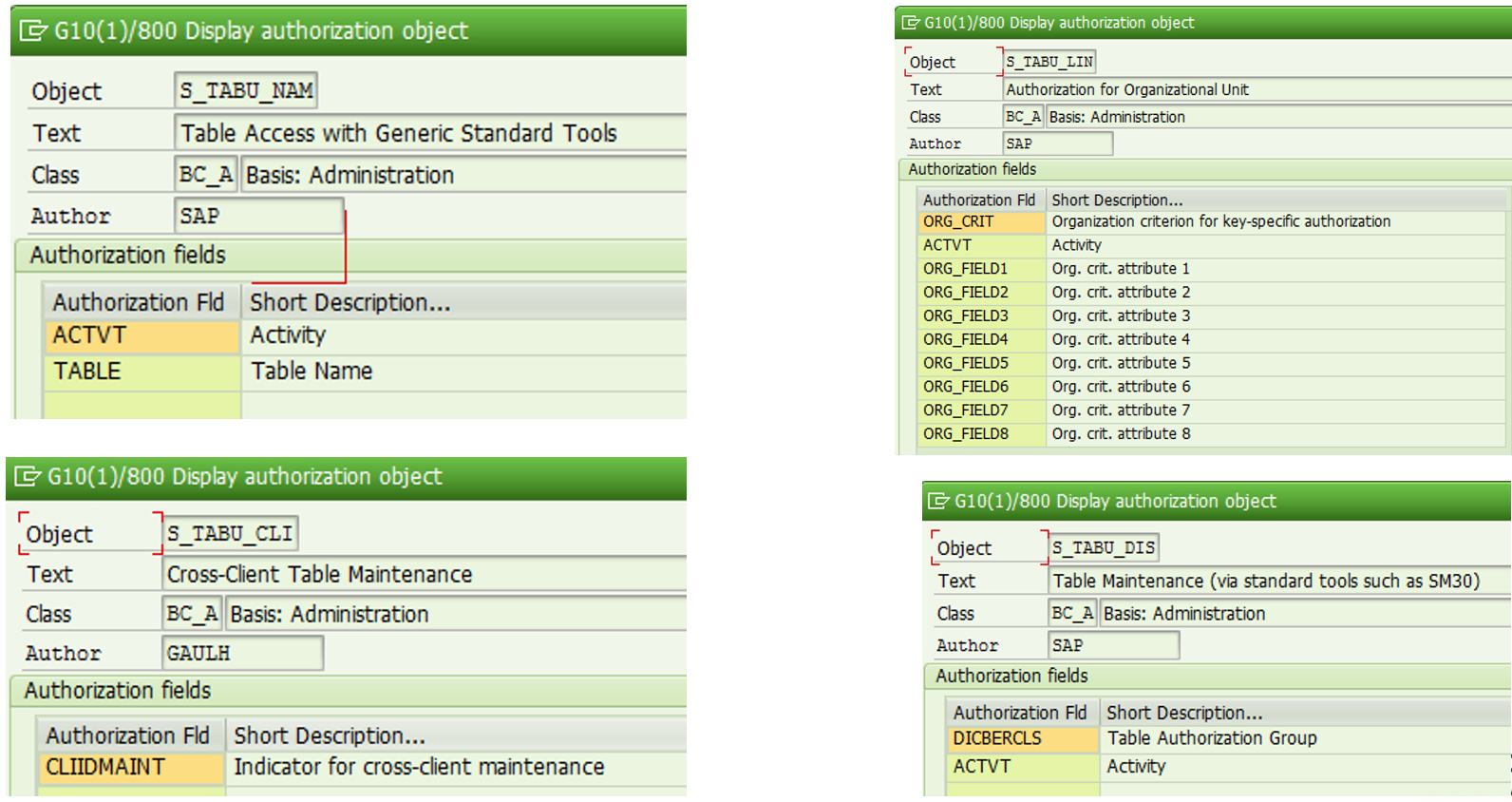
This one's a bad habit. Most common causes are:
- Project necessities not better detailed
- Scarse sensibility towards data security
- Scarse knowledge of potential problems of this action
Why should you remove these users, even non-interactive ones, ASAP? Let's see some examples!
Read More
Topics:
sap_all,
auditing,
rfc,
rfc destination,
rfc security,
system users
Why is it a strategic move to have a document that describes how the SAP security was addressed in the company?
When is it needed? What is it needed for? Why do it? How do you maintain it?
Read More
Topics:
sap security guidelines,
SAP Security Documentation
Employees management inside the HR systems (Human Resources). Here it's also essential to manage access in a way that protects sensible data.
Which are the instruments inside SAP HR systems used for logs management? Let's see the main ones here.
Read More
Topics:
security audit log,
audit sap,
UI logging,
SAP LOG
Segregation of Duties project: how many risks need to be defined?
Read More
Topics:
Segregation of duties,
SAP Security,
audit,
custom transactions
Security for custom code in SAP has always been underestimated in most installations
Only recently, in the last years, customers are starting to understand the true importance of code security, mostly related to ABAP language in SAP case.
The SAP ABAP developer then becomes a strategic figure in making sure that programs security (especially custom code security) is attended to and correctly managed.
How do you make sure to always be on top of the topic?
Read More
Topics:
secure coding sap,
SAP Security,
sap developer,
Secure programming
Do many days pass from the moment you create a new transaction to when the end user finally is executing it?
Something in the test creation and release processes may have not worked as it should have.
How can you avoid this?
Read More
Topics:
sicurezza sap,
test system,
quality,
su53
Do you execute transaction PFCG daily, or even sometimes? Perhaps you're not aware of these functionalities that might be useful in some cases.
During the ordinary system management this information might turn out to be useful.
Read More
Topics:
pfcg,
PFCG SAP transaction,
role translation
For those that don't know SAP's authorization aspects this title might be just a tongue-twister.
On the contrary for those who manage authorizations in SAP these are very well-known authorization objects. How should you go about managing them?
Read More
Topics:
se16,
s_tabu_dis,
s_tabu_rfc,
s_tabu_nam,
sql
Who said that in order to have powerful systems you need to have many resources?
How can a small enterprise be compete with a big corporation?
Read More
Topics:
sap cyber security,
siem,
threat detection,
security bridge
The aim of the SoD is to make sure that only people with the right are of competence have access to sensitive transactions.
Read More
Topics:
Segregation of duties,
Security Analyzer