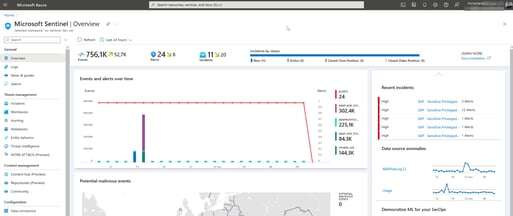
Microsoft Sentinel and SAP: How can these systems be leveraged to have continuous threat monitoring in SAP systems? How do you protect data security in SAP with this tool?
A recent but promising solution for Continuous Threat Monitoring management for SAP systems.