Currently, there is no one-size-fits-all solution to address all the issues required by the GDPR.

SAP proposes different systems, see what they are and what they are used for. SAP offers different systems: what are those and what are they for?
The GDPR compliance management process
The GDPR conformity management expectes the involvement of several company directorates. The main macro-phases, from the identification and management of personal data's point of view are the following:
- Identification of relevant GDPR processes
- Adaptation of the contracts (suppliers, employees, customers)
- Identification of managed personal data
- Identification of the personal data present in the various business systems used (Personal data not processed electronically must also be handled)
- Definition of treatments' register
- Data Privacy Impact Analysis (DPIA)
- Management of the treatments emerged during the risk analysis
- Adjustment of company policies Adeguamento delle policy aziendali (es. Data Breach Policy, definition of new GDPR compliant projects)
- Training for the involved actors
From the SAP's technical point of view what can you do?
SAP has several tools that try to satisfy most of the previous steps.
The adoption of the instruments defined by SAP doesn't imply automatic adaptation to the Regulation.
Each Company must carry out a risk assessment to determine if it has to carry out risk mitigation actions.
What are the SAP tools/systems for managing the GDPR?
Specific systems have been designed for each of the macro areas above.
- Identification of personal data
- SAP Information Steward
- SAP Process Mining by Celonis
- SAP Power Designer
- Treatments' Register (RoPA - Records of processing activities)
- Control definition e DPIA
- SAP Process Control e Risk Management, Audit Management
- Right to oblivion and data retention
- SAP ILM - Information Lifecycle Management
- Scrambling of data in a non-productive environment
- SAP TDMS Test Data Migration Server
- Masking of SAP data
- SAP Field Masking
- Security in SAP's landscapes and Accountability
- SAP SSO - Single Sing On
- SAP IDM - Identity Management System
- SAP GRC Access Control
- SAP Fraud Management
- SAP CVA - Code Vulnerability Analysis
- SAP Cloud Platform Identity Management Services
All the above tools are applicable only to SAP Systems. Except for systems such as Information Steward, IDM, SSO, GRC, which can also be connected to non-SAP systems.
However the data masking, retention and scrambling part is performed only in SAP systems.
Identification of personal data
Are systems that allow, for example for the Information Stewart, to understand where a certain data is found in the various databases SAP and not SAP.
Imagine the example of the fiscal code. The structure of this information can be identified by the use of regular expressions. This tool allows to identify if the content of a field in a database can be assimilated to the entered search key, in this case a fiscal code. Watch here a demo video.
In which processes are personal data present? This is the question that the SAP solution, SAP Process Mining by Celonis, can answer. Watch here the video
SAP Data Privacy and Governance
It's a tool totally in cloud. Consist of the following modules:
- Policy definition and distribution among users definition
- All Data collection in order to define RoPA (treatments' register)
- PIA Definition - Privacy Impact Analysis (also valid for ISO27001, security side)
- Limitation checks to be carried out (a catalogue of ready-made mitigation controls is being developed by SAP)
One of the key point of the tool is that every process owner receive a document/ quiz that could answer questions to establish the register of processing operations.
SAP Information Lifecycle Management
SAP ILM allows to manage the data retention rules. This system exploits the data storage mechanism to export data from SAP making it accessible or not to a small group of users. It allows managing the data retention rules. Definition of:
- residence rule, or the duration within the data have to remain live in the system
- retention rule, or the duration within the data have to be kept in the archive before its possible destruction
Then, the data aren't erased from the database I dati quindi non sono cancellati dal database but are archived. There are other systems on the market to perform the same operation but modifying the data in the database.
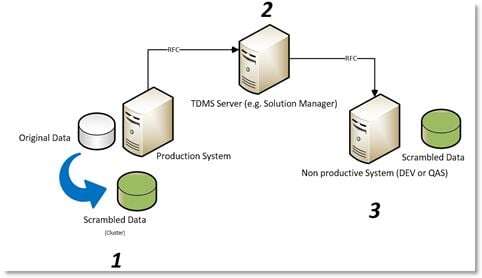
SAP TDMS Test Data Migration Server
Data protection in non-productive systems occurs using tools that change the content of the data while copying the systems. This in done by scrambling rules. What are these rules? For example:
- Random, or replace with random data
- Table conversion, in this case "was - become". For example: the name John White becomes Jack Brown in questo caso ho un "era diventa".
- Custom rules to be defined by writing ad hoc ABAP programs
How does the TDMS process occur?
- Stand-Alone Scrambling, in this case a copy is made, as provided in the standard SAP or else without TDMS and the latter intervenes directly in the copied system to modify the data
- Scrambling During Data Transfer, in this case data scrambling is applied during the system copying phase.
What are the main points to consider?
If you are an IT manager you should:
- Know what are the personal data that need to be protected, this phase it is not only under the IT’s responsibility. There should be cooperation between different departments.
- Identify them in the various systems involved. The technical translation of the data collected in the previous phase and the identification in the various systems.
- Analyze the results of risk analysis to see if there are actions to be taken for example activate cryptography, anonymize data
- Assess where to define a register of treatments? Perhaps a simple excel file is not enough to perform and integrate all the required data
Only as a result of the above should you consider the tools you may need to carry out the above.
Blog post originally translated from: https://www.aglea.com/blog/gdpr-sap-quali-sono-i-sistemi/strumenti-coinvolti
