
SAP Cyber Security
Indice
Which are the main tools/configurations to activate?
In some cases there are simply functionalities to activate in SAP, which are already present in the system. In other cases it's necessary to activate solutions (often included in the SAP suite). In others it's needed to buy specific softwares.
Therefore there are different scenarios that can be used depending on the context and on the attack surface that you want to preside over.
How can Aglea help you in the management of Cyber Security in SAP?
People that take care of IT security as their job know that often in a company there aren't sufficient resources to tackle all the thematics that should be managed.
In SAP's case, it's seen as an "internal" product in the company. Therefore it's not directly exposed. Or like a "black box" that "people who know SAP" know about and that must not be touched or else the business processes stop.
This is partially true. But on the other hand, by taking on the argument step by step, you can discover that there is a path and if followed correctly you can obtain important results.
This is exactly what we do, trying to bring two very different worlds closer to each other, the IT security world and the SAP world. Doing this with a precise and guided path, also for who doens't know about SAP, but knows the aspects of IT security.
Contact us if you want to knwo more or discuss the above thematics!
Articoli Suggeriti
SAP Cybersecurity - SAP Enterprise Threat Detection cosa è?
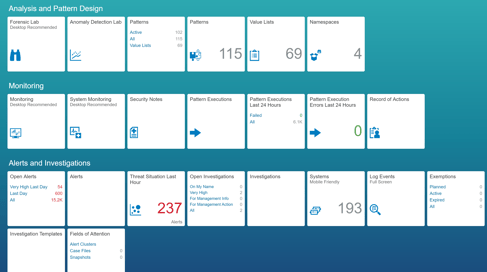
Cosa puoi fare quando si parla di Cyber Security in ambito SAP?
Esiste uno strumento che SAP ha sviluppato chiamato SAP Enterprise Threat Detection che può essere utilizzato.
Cyber Security SAP ERP

Cosa significa questo termine?
Quali sono le azioni che possiamo fare per proteggere un sistema SAP?
SAP Cyber Security, solo l'IT è coinvolto? Cyber Security Culture

In passato erano sicuramente una nicchia le tematiche legate alla sicurezza dei dati. Oggi gli aspetti di Cyber Security sono tenuti in considerazione in maniera molto maggiore, in parte anche per i nuovi paradigmi di accesso es. le soluzioni SAP cloud.
Ma quanto parlare di Cyber Security fa riferimento al solo dipartimento IT? Probabilmente una visione completa di questi aspetti deve andare ben oltre il solo dipartimento dei sistemi informativi.
